Check Email Security Using CheckTLS: A Comprehensive Non-Technical Reference
TL;DR; Step-by-step instructions for using CheckTLS to test the security of email systems including TLS, DNSSEC, MTA-STS, DANE,SPF, DKIM, DMARC, BIMI.
Instructions are provided to run ("TestReceiver") to test:
Instructions are provided to run ("TestSender") to test:
A button opens actual test results side-by-side with these instructions so users can see exactly what is being described.
How CheckTLS Tests are Organized
Each CheckTLS test is associated with one of two email "modes" — sending email or receiving email (the exception to this rule is the TLS test and the DNSSEC test, which are associated with both email modes). CheckTLS has labeled the two CheckTLS tests associated with these two email modes "TestReceiver" and "TestSender". TestReceiver tests the security of receiving email servers. TestSender tests the security of sending email servers.
These two test modes (TestReceiver and Testsender) each test multiple Email Security Technologies. The technologies are shown below, and each technology is linked to a detailed explanation, below, of how a test mode (TestReceiver or TestSender) tests that technology and the results that the testing produces.
To help CheckTLS users remember whether they are testing a receiving email server or a sending email server, the testing options listed when the CheckTLS website's "email" main menu item is clicked are labeled "testTo:" for TestReceiver tests (the user is testing the server that receives email sent To: it), and labeled "TestFrom:" for TestSender tests (the user is testing the server that sends email sent From: it).
How to Run the TestReceiver CheckTLS Tests
When you select "TestTo:" option from the CheckTLS website's "email" main menu item, you are brought to the TestReceiver webpage. The "Input Fields" dialog box, shown below, is where you specify and configure which technologies you want TestReceiver to test in the receiving email server (the "eMail Target:" in the dialog box). Clicking the "More Options (MTA-STS, ...)" text expands the dialog box to display all of the TestReceiver tests that can be performed when the "Run Test" button is clicked.
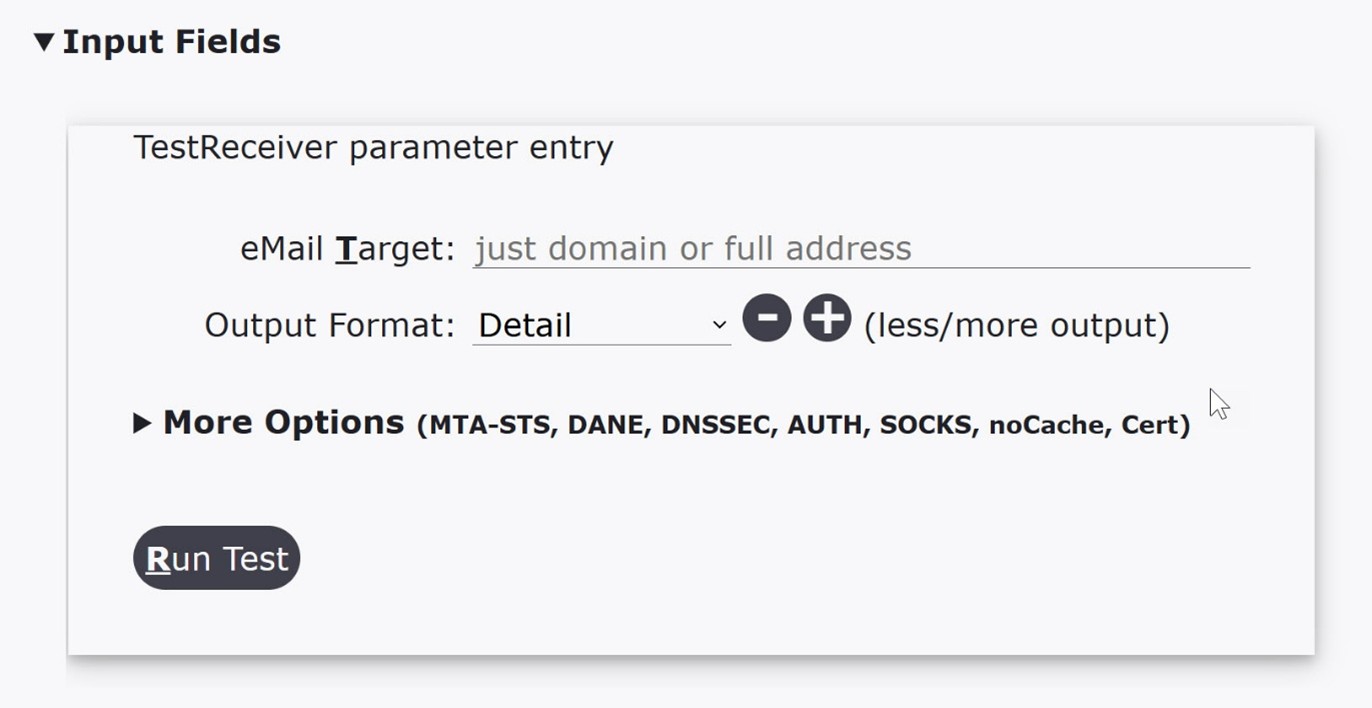
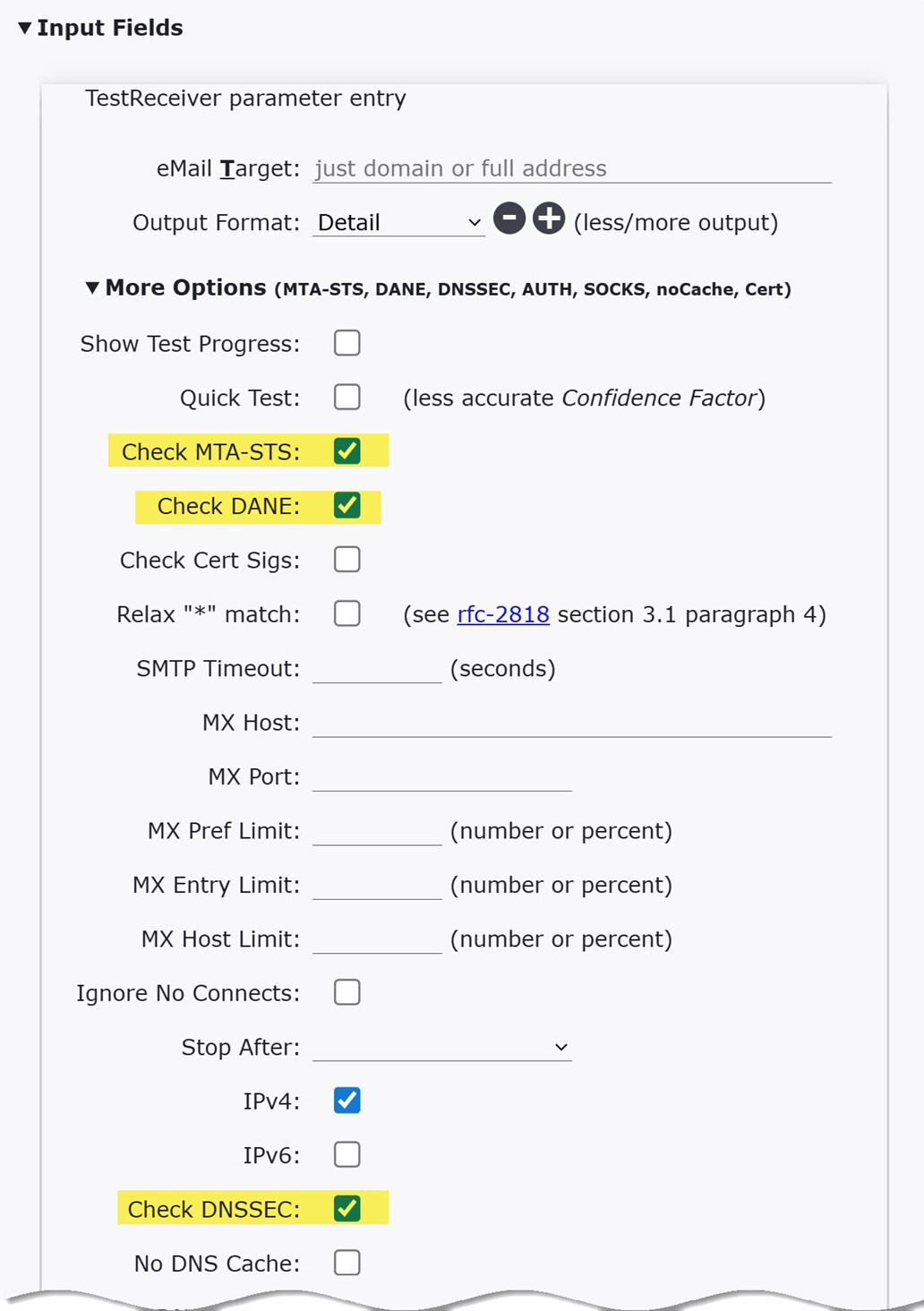
Only the upper portion of the expanded "More Options (MTA-STS, ...)" is shown in the image above — there are many more options that can be included when you run TestReceiver. When you expand the "More Options (MTA-STS, ...)" you won't see an option to test TLS. That is because the TestReceiver automatically tests TLS every time it is run. Before you run TestReceiver, be sure that you have entered an email domain (preferred), a full email address (e.g. user@company.com), or an individual email server (hostname or ip address) in the "eMail Target" entry line. Leave the "Output Format" set to "Detail" so that you can view all of the results that get returned when TestReceiver is run. If you want to understand what each Input Field Option means and how it is used, click the "Instructions/Info" link located above the "Input Fields" label. A link to the complete documentation for TestReceiver will be provided.
THE RESULTS OF YOUR TestReceiver TESTING WILL BE DISPLAYED ON-SCREEN IN THE SECTION OF THE WEBPAGE LABELED "Test Results".
How to Run the TestSender CheckTLS Tests
When you select the "testFrom:" from the CheckTLS website's "email" main menu item you are brought to the TestSender webpage. The "Input Fields" dialog box, shown below, is where you specify and configure which technologies you want TestSender to test in your email server.
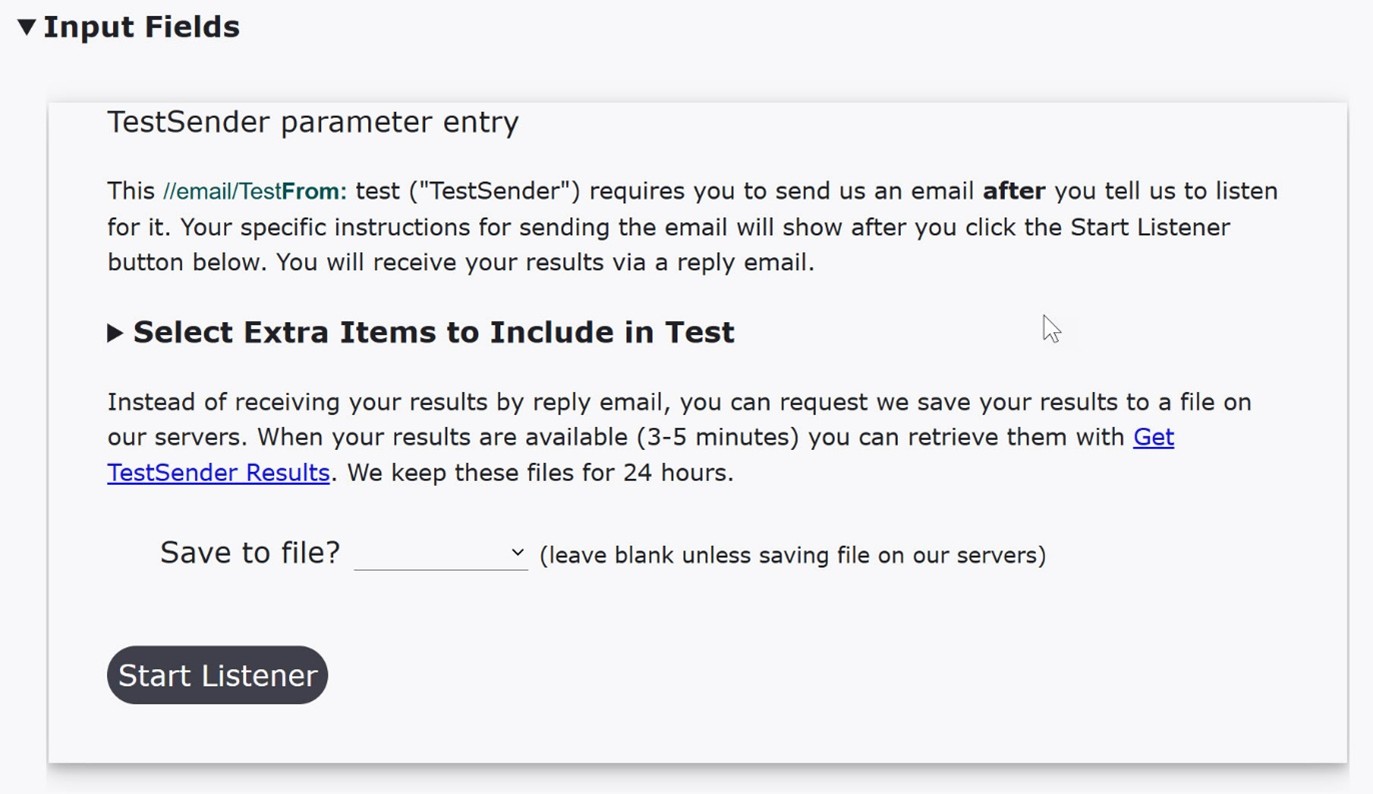
Because TestSender tests the security of your email server, there is no eMail Target: entry line for TestSender (like there is for TestReceiver tests). The "target" of TestSender tests is your sending email server. In order for CheckTLS to be able to test the security of your email server, you must send us a specially-crafted email using an email account on the email server whose security you wish to test. If you have multiple sending email servers, you must run TestSender tests, and therefor send us an email, from each server. Like TestReceiver, TestSender automatically tests the status of TLS. Clicking the "Select Extra Items to Include in Test" text displays a list of individual Email Security Technologies that can be tested with each TestSender run.
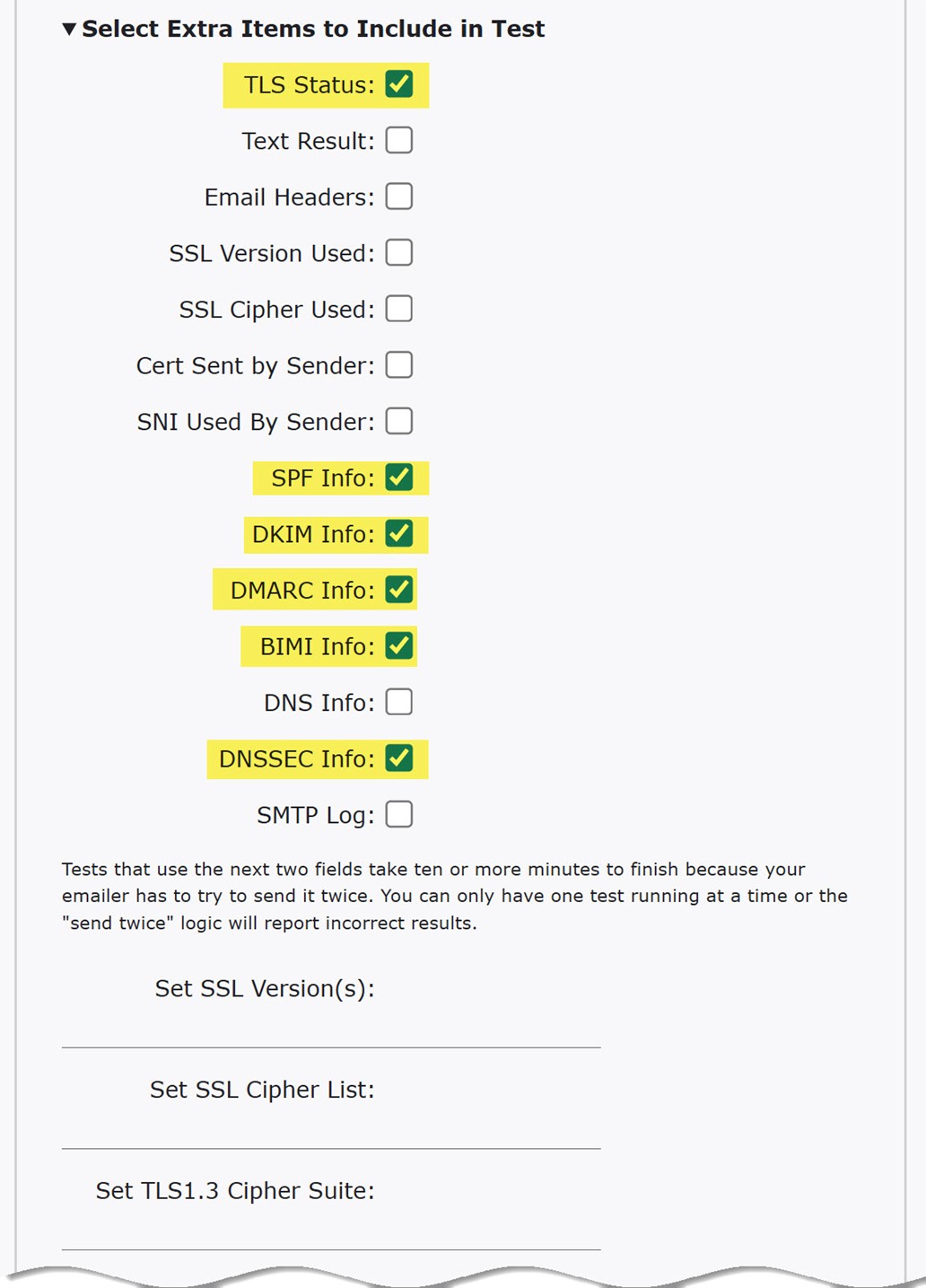
In the image above, TestSender will display results for the selected TLS, SPF, DKIM, DMARC, BIMI, and DNSSEC technologies. The technologies you select are specified in the specially-crafted email (explanation of the email is in the next paragraph) that you send to us that initiates TestSender testing. Once a TestSender test has completed, we send the result of the test back to you in a Reply email. If you want to understand what each Input Field Extra Item means and how it is used, click the "Instruction/Info" link located above the "Input Fields" label. A link to the complete documentation for TestSender will be provided.
What is the Listener and why do I have to start it? The Listener is started on our CheckTLS TestSender servers, not on your email server. It listens for the specially-crafted email that you send to our TestSender servers. When you send the specially-crafted email, our Listener detects that the your email is being transmitted to us and we perform the TestSender tests. We use the information contained in the email to tell us how to report the results of our tests back to you. When you click the "Start Listener" button, two things happen:
- The Listener is started on our CheckTLS TestSender servers
- Instructions for creating the specially-crafted email are displayed on your computer (you may have to scroll down to view the instructions)
If your MAILTO: app has been associated with an email client, you can create the specially-crafted email automatically by clicking the "Click here to create the email" text near the bottom of the instructions. This will automatically start a new email and pre-populate it with the correct specially-crafted message, which will include:
- From:
- set to your default email account
- To:
- set to test@TestSender.CheckTLS.com
- Subject:
- unique password for just this one test
- text strings
- that indicate the "Select Extra Items to Include"
- default body text
- "This is a test message."
This is the specially-crafted email.
NOTE: If you have not associated an email client with MAILTO: links on webpages, some versions of Windows will automatically associate your Microsoft account email address with MAILTO: links on webpages if you click any MAILTO: link, including our "Click here to create the email" link.
If you do not want to use this default association, you can change the MAILTO: app to another email client by navigating to Settings>Apps>Default apps>Choose defaults by link type. Scroll down to the MAILTO: tile and click it.
If you do not have an email client associated with MAILTO: links on webpages, you will need to create the specially-crafted email manually. Start a new email that will be sent from an email account on the email server you want TestSender to test (the "From:" address in your email). Use the exact same values displayed in the instructions for the To:, Subject:, and email body.
When your specially-crafted email is complete, SEND it. Check your inbox in a minute or two for a Reply from our TestSender server with the results of your TestSender test. If the Reply email doesn't show up in your inbox, check your spam folder (and whitelist CheckTLS in the future if you know how). If the email does not show up anywhere, you can see if your email system "bounced" our results message by clicking the "HERE" link in the "check your logs for a bounce from your domain HERE" text at the very bottom of the instructions for creating the specially-crafted email page.
Viewing CheckTLS Test Results
Located at the end of this blog post are examples of the results produced by TestReceiver and TestSenter tests for the checktls.com website. We've included these example test results so that you can see exactly what your test results will look like (obviously with your data). As a reminder, the test results for TestReceiver tests will be presented on-screen shortly after you click the "Run Test" button. The test results for TestSender tests will not be displayed on-screen but will be retuned to you in a Reply email to the specially-crafted email that you send us.
In the following sections of this document the individual Email Security Technologies that are tested with the TestReceiver and TestSender email modes are explained in detail. In the explanation for each Email Security Technology there will be at least one "See It Below" button present. When clicked, the "See It Below" button will highlight (in a vivid blue color) the test results that are produced by the CheckTLS test that the "See It Below" button is associated with. An individual TestReceiver or TestSender run may test multiple Email Security Technologies. NOTE: When you click the "See It Below" button, your browser will display a small window with a message that says "(x) lines marked in results." This tells you how many lines are highlighted in the example test results so that you know how many test details to look for.
Because an individual TestReceiver or TestSender run may test multiple Email Security Technologies, and those highlighted results may be located far apart in the example checktls.com test results located at the end of this webpage, you will have to manually scroll the webpage down to veiw the highlighted test results.
If you find it inconvenient to keep scrolling down and then finding your place back above, this document can be opened in two side-by-side windows, with the second window only displaying the example checktls.com test results. This enables you to keep your place where you are reading on the "Using CheckTLS" web page while being able to use the second web page (we call it a "Second Window") to view highlighted test results. To open a second web page that displays example checktls.com TestReceiver and TestSender test results click the "Second Window" button, below.
TestReceiver CheckTLS Email Security Technologies
How to test each of the individual Email Security Technologies that TestReceiver can test is described in detail below. As a reminder, TestReceiver tests are performed on receiving email servers. TestReceiver reports on how well an email server that receives your email implements an Email Security Technology.
Receiving Server: TLS (Transport Layer Security) Test
TestReceiver tests the degree to which receiving email servers use TLS.
Recall that TLS does three things: 1.) It encrypts the contents of an email so that the contents cannot be understood by any human or machine. 2.) It protects the contents from being altered so that the recipient receives exactly what the sender sent, and 3.) It authenticates that the receiving email server is allowed to receive email for the domain(s) that are present in the receiver's email address(es).
When you click the TestReceiver test's "Run Test" button, CheckTLS testss the TLS implementation of each email server specified by the "eMail Target" field. If the "eMail Target" has MX records attached to it in DNS, CheckTLS will check every email server that the recipient organization says can receive email (a recipient organization may have more than one receiving email server specified by its domain DNS MX record(s)). The results of the test can be displayed in real-time as the probing is performed. Once all probing is complete, the page is scrolled back to the top where a summary of the test results are displayed. The results page has a lot more information than just the summary of the tests results, but for TLS the important result on the test results page is the column in the summary labeled "TLS", which shows either "OK" or "FAIL".
When you ran the TestReceiver test, if you kept the "Output Format" field set to its default value of "Detail", you can scroll down the results page and see what information CheckTLS used to determine the status of TLS. So what should you look for in the Details to determine the quality of the receiver's TLS implementation?
Certificate Validity Check that every certificate is:
- not expired (or not too early either)
- signed by a trusted Certificate Authority (CA)
- not revoked
Site Certificate Details Check that the first certificate has a:
- Common Name (CN) or Subject Alternative Name (SAN) that matches the server's domain name
- Algorithm & Key length that is RSA & 2048 bits or more, or ECC (e.g. P-256) and 256 bits or more. (Avoid outdated algorithms like SHA-1 or MD5.)
- complete certificate chain to the trusted Certificate Authority (CA)
Protocol & Cipher Strength Check that the TLS connection has:
- Protocol version TLS 1.2 or higher. (Reject SSLv2, SSLv3, TLS 1.0, TLS 1.1)
- Strong ciphersuites, e.g. AES-GEM, ChaCha20-Poly1305. (Avoid weak ones like RC4, 3DES, NULL, EXPORT.)
- Forward secrecy. Look for ECDHE/DHE key exchange.
We encourage users to review the TestReceiver Documentation to learn what the individual Detail test results mean and more about what CheckTLS can do.
CheckTLS Testing DNSSEC (Domain Name System SECurity Extensions) for receiving email
Recall that DNS is a critical component of all the Email Security Technologies, and DNS is used by both Senders and Receivers in protecting and delivering email. Both the CheckTLS ("TestReceiver") test and the CheckTLS ("TestSender") test can test their respective target's (sending or receiving) DNSSEC.
To test DNSSEC for how your DNS answers DNS queries that are used by email receivers, use the CheckTLS ("TestSender") test. Use the TestSender instructions above to select the DNSSEC option and display the TestSender Setup Page. This link will go to the TestSender page, select the SPF option, and bring up the TestSender Setup Page for you.
In the TestSender output, CheckTLS reports on the status of DNSSEC on every DNS lookup that an email receiver performs when receiving email from your domain.
CheckTLS Testing MTA-STS (Strict Transport Security)
To verify that your MTA-STS (Mail Transfer Agent Strict Transport Security) is set up correctly, use the CheckTLS ("TestReceiver") test. Use the TestReceiver instructions above to test (Target) your own domain and select the MTA-STS option to see what an email sender will get when checking your MTA-STS.
CheckTLS reports if your MTA-STS is correct right at the top of the result in the Matrix section:
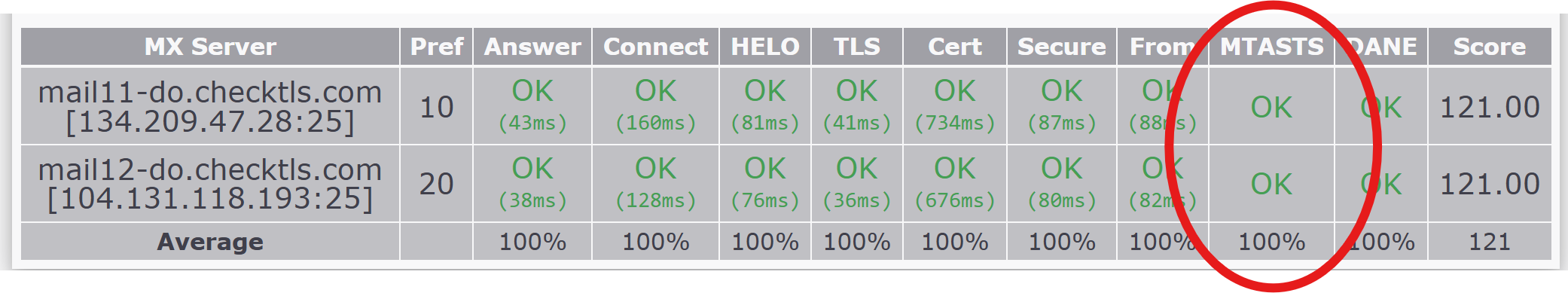
In checking if your MTA-STS is correct, CheckTLS looks at:
-
MTA-STS DNS Record: Verifies that you have the appropriate DNS TXT record for your domain to indicate that you are using MTA-STS.
It should look something like:
_mta-sts.<yourdomain>. IN TXT "v=STSv1; id=20231015T000000Z;" -
MTA-STS Policy File (mta-sts.txt):
-
Verifies that you have an MTA-STS policy file, usually named mta-sts.txt, hosted at a specific location:
https://mta-sts.<yourdomain>/.well-known/mta-sts.txtThis file must be accessible using HTTPS without any errors. -
Verifies the contents of the mta-sts.txt file, something like:
version: STSv1 mode: enforce mx: mail.<yourdomain> ttl: 86400The mode can be one of enforce, testing, or none. enforce is recommended for full security.
-
Verifies that you have an MTA-STS policy file, usually named mta-sts.txt, hosted at a specific location:
- MX Records: Verifies that your MX records (Mail Exchanger records) are set correctly for your domain. The MX records should point to the correct mail servers, which should match what's specified in your MTA-STS policy file (mx: field).
- Certificate Verification: Verifies that your mail servers have valid, trusted SSL/TLS certificates.
CheckTLS Testing DANE (DNS-based Authentication of Named Entities)
To verify that your DANE (DNS-based Authentication of Named Entities) for SMTP is setup correctly, use the CheckTLS ("TestReceiver") test. Use the TestReceiver instructions above to test (Target) your own domain and select the DANE option to see what an email sender will get when checking your DANE.
CheckTLS reports if your DANE is correct right at the top of the result in the Matrix section:
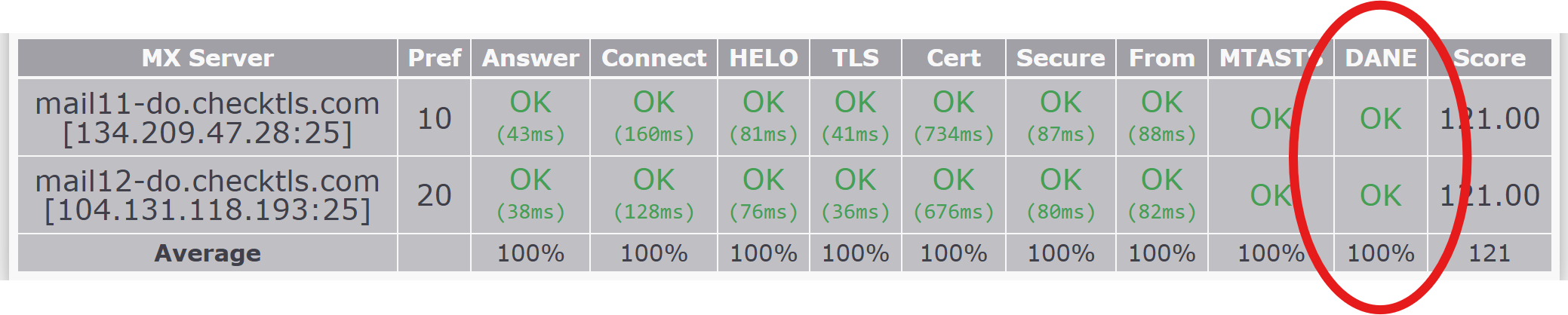
In checking if your DANE is correct, CheckTLS looks at:
-
MX Records: Verify that your domain has valid MX records:
- pointing to the correct mail servers
- MX hosts have valid A/AAAA records
- DNSSEC: Verify that your DNS is signed correctly for your domain and your MX hostnames.
-
TLSA Records: Verify that the DANE DNS TLSA records exist for all MX hostnames and are correct:
_25._tcp.mail.example.com. IN TLSA 3 1 1 5e2b8b79c406a4a2e5d51f77d1bb8f2ed67e36d8e232ef09acb9e2fda88a0b0f - MX Certificate matches TLSA record:
- Verify that the certificate is valid (not expired, name matches).
- Verify that the public key or certificate fingerprint matches the TLSA record hash.
- STARTTLS Support: Verify that TLS is supported and enabled
CheckTLS Testing TLS (Transport Layer Security) for sending email
Recall that TLS does three things: It encrypts the contents of an email, making it so the email contents can not be seen by any human or machine. It protects the contents from being altered, so that the recipient gets exactly what the sender sent. And it authenticates that the server to which the receiver is preparing to send the email is allowed to receive email for the domain in the email address.
The CheckTLS ("TestSender") test is used to test a Sender’s TLS. By default TestSender tests TLS. Use the TestSender instructions above to select any additional TLS options, like SSL Versions and Ciphers, and then display the TestSender Setup Page. This link will go to the TestSender page and bring up the TestSender Setup Page for you.
In checking if your Sender TLS is correct, CheckTLS looks at whether or not it could establish a valid SSL/TLS connection to receive the test email that you send to CheckTLS.
Because the primary purpose of TestSender is to test TLS, the result is reported as success or failure; success meaning a SSL/TLS connection was used to receive your email, and failure meaning CheckTLS could not establish a good SSL/TLS connection with your server.
If you selected any additional TLS options before starting the test email to CheckTLS, these are reported along with the success or failure message.
CheckTLS Testing DNSSEC (Domain Name System SECurity Extensions) for sending email
Recall that DNS is a critical component of all the Email Security Technologies, and DNS is used by both Senders and Receivers in protecting and delivering email. Both the CheckTLS ("TestReceiver") test and the CheckTLS ("TestSender") test can test their respective target's (sending or receiving) DNSSEC.
To test DNSSEC for how your DNS answers DNS queries that are used by email senders, use the CheckTLS ("TestReceiver") test. Use the TestReceiver instructions above to test (Target) your own domain and select the DNSSEC option to see what an email sender will get when doing DNS queries for your domain.
In the TestReceiver output, CheckTLS reports on the status of DNSSEC on every DNS lookup that an email sender performs when sending email to your domain.
CheckTLS Testing SPF (Sender Policy Framework)
Recall that Senders use SPF to list the IP addresses of the servers that can send email for the Sender’s domain. Any email that does not come from one of those listed servers is suspect and is almost certainly “bad”.
The CheckTLS ("TestSender") test is used to test a Sender’s SPF. Use the TestSender instructions above to select the SPF option and display the TestSender Setup Page. This link will go to the TestSender page, select the SPF option, and bring up the TestSender Setup Page for you.
SPF checks can be performed against the MAIL FROM (or Return-Path) domain and/or the HELO/EHLO hostname.
CheckTLS reports if your SPF is correct for both of these checks:
SPF mfrom result pass
SPF helo result pass
The SPF MAIL FROM check is better at checking the validity of an email because it looks at the physical IP address from which the sender is connecting and not the IP address from where the sender says it is connecting.
Typically an SPF check will try the MAIL FROM first and then if that is missing it will try the HELO/EHLO.
In checking if your SPF MAIL FROM is correct, CheckTLS looks at:
- SPF DNS: record(s) exist for the domain in the MAIL FROM and are correctly formatted.
- IP address: did the connection from the sender come from an IP address listed in the SPF DNS record(s).
In checking if your SPF HELO/EHLO is correct, CheckTLS looks at:
- SPF DNS: record(s) exist for the hostname in the HELO/EHLO SMTP command and are correctly formatted.
- IP address: did a DNS lookup of the HELO/EHLO hostname match an IP address listed in the SPF DNS record(s).
CheckTLS Testing DKIM (DomainKeys Identified Mail)
Recall that Senders use DKIM to make sure your domain's outgoing email is properly authenticated and trusted by receiving mail servers. The CheckTLS ("TestSender") test is used to test a Sender’s DKIM. Use the TestSender instructions above to select the DKIM option and display the TestSender Setup Page. This link will go to the TestSender page, select the DKIM option, and bring up the TestSender Setup Page for you.
Every DKIM setup begins with a selector (e.g., selector1) and a corresponding DNS TXT record at: selector1._domainkey.yourdomain.com. In checking if your DKIM is correct, CheckTLS looks at:
-
DKIM DNS TXT record: Verify that your domain has a valid DKIM DNS TXT record:
- exists at the proper lookup, e.g. selector1._domainkey.yourdomain.com
-
is properly formatted and accurate with these fields:
- v=DKIM1 (version)
- k=cryptotype (the cryptographic key type used to sign)
- p=publickey (the public key of the private key used to sign your email)
-
emails are signed:
- adds an RFC-822 email header: "DKIM-Signature"
-
header is properly formatted and accurate with these fields:
- v=1 (version)
- a=algorithm (uses a modern algorithm, e.g. rsa-sha256)
- c=canonicalization (the canonicalization algorithm used to generate header hashes, usually "relaxed")
- d=yourdomain (matches your domain)
- s=selector (matches a selector in a DKIM DNS record)
- t=timestamp (when the signature was created, usually a unix timestamp seconds since the epoch GMT)
- h=headers (the email headers included in the message hash)
- bh=hash (the hash value computed for the selected headers and full body of the message)
- b=signature (the private key signature of the hash)
-
email signature matches the contents of the received email and selected headers by:
- computing a new hash of the message body using the a=algorithm in the DKIM-Signature header
- verify that the new hash matches the bh=hash in the DKIM-Signature header
- select and make canonical the headers listed in the h=headers field of the DKIM-Signature header
- compute a new hash digest of the selected headers
- use the s=selector and d=domain fields in the DKIM-Signature header to fetch the sender's public key from DNS
- using the public key specified in the DKIM DNS record, decrypt the signature from the b=signature field in the DKIM-Signature header
- verify that the new hash digest matches the decrypted hash digest
To understand how DKIM unequivocally assures that the message received is exactly what the sender sent, follow the above steps in reverse.
- The decrypted hash digest is known to be correct because pubic/private key encryption assures that the decrypted hash digest was encrypted by the sender's private key.
- The sender's private key is known to be correct because it comes from a separate, non-email, system (DNS) and can be further protected by DNSSEC.
- The important message headers in the received message are known to be unchanged from what the sender sent because a newly computed hash digest of the selected headers matches the decrypted hash digest.
- The body hash digest in the DKIM-Signature header is known to be correct because it is one of the important message headers that are known to be unchanged.
- The body of the message is known to be correct because the newly computed body hash digest matches the body hash digest in the DKIM-Signature header.
CheckTLS Testing DMARC (Domain-based Message Authentication, Reporting, and Conformance)
Recall that Senders use DMARC to mandate SPF and/or DKIM, the two underlying email authentication methods, and requires one or both. It also enforces alignment between SPF/DKIM and the visible "From:" domain, and it tells receiving mail servers what to do if authentication fails. DMARC does not do authentication itself, rather it checks the results of SPF or DKIM or both, and that they match the domain in the From: header.
DMARC improves email authentication by announcing to the world, via a DNS DMARC record, that a domain does SPF and/or DKIM, so receivers know to check any received emails from that domain for SPF and/or DKIM. It also improves authentication by matching the From: address in the email to the domain, telling receivers "If you get an email from my domain, be sure to check SPF and/or DKIM", and "Any email from my domain has to explicitly come from a particular From: domain and only a particular From: domain". This prevents a sender from spoofing a sub-domain of your domain, for example "sales@spoofed.checktls.com".
The CheckTLS ("TestSender") test is used to test a Sender’s DMARC. Use the TestSender instructions above to select the DMARC option and display the TestSender Setup Page. Obviously because DMARC sits on top of SPF and/or DKIM, selecting one or both of these is also useful. This link will go to the TestSender page, select the DKIM option, and bring up the TestSender Setup Page for you.
In checking that your DMARC is correct, CheckTLS checks that one or both of:
- SPF was able to authenticate the message (message came from the right IP address) and the return-path domain aligns with (matches) the From: message header
- DKIM was able to authenticate the message (message was not changed) and the d= signing domain aligns with (matches) the From: message header
When checking alignment, CheckTLS uses either "strict" or "relaxed" matching based on the aspf= (for SPF) or the adkim= (for DKIM) fields on the domain's DMARC DNS record. "strict" means the domains must exactly match from beginning to end, while "relaxed" means a subdomain can match a parent domains. For example sales.mycompany.com is a relaxed match of mycompany.com, but it is not a strict match.
CheckTLS reports on the DMARC policy but it does not follow the policy since the email is just a test email and is not saved on our system.
CheckTLS also reports on the DMARC reporting specified by your DMARC, but again it does not do any actual reporting.
CheckTLS Testing BIMI (Brand Indicators for Message Identification)
Recall that Senders use BIMI to mandate DMARC (which mandates SPF and/or DKIM also). Receivers that check BIMI will display your company's logo next to any emails received from your company that meet your BIMI requirements. Receivers will not display your logo, and possibly display an error, or quarantine, any emails received that do not meet your BIMI requirements.
The CheckTLS ("TestSender") test is used to test a Sender’s BIMI. Use the TestSender instructions above to select the BIMI option and display the TestSender Setup Page. Obviously because BIMI sits on top of DMARC, and therefore SPF and/or DKIM, selecting one or more of these is also useful. This link will go to the TestSender page, select the BIMI option, and bring up the TestSender Setup Page for you.
In checking that your BIMI is correct, CheckTLS looks at:
- if you have a valid BIMI record in DNS
- that your email system correctly implements DMARC (which checks SPF and/or DKIM)
- optionally that you have a Verified Mark Certificate (CheckTLS does not check this yet)
Example results from the CheckTLS ("TestReceiver") Test
(scroll left and right to see wide data)| seconds | lookup | result | |
|---|---|---|---|
| [000.001] | DNS LOOKUPS | ||
| [000.042] | SEARCHLIST | 104.131.108.216,134.209.169.224,1.1.1.1,8.8.8.8,67.207.67.3 | |
| [000.242] | MTASTS policy-->url | https://mta-sts.checktls.com/.well-known/mta-sts.txt | |
| [000.242] | MTASTS policy-->status | 200 OK | |
| [000.243] | MTASTS policy-->version | STSv1 | |
| [000.243] | MTASTS policy-->mode | testing | |
| [000.243] | MTASTS policy-->max_age | 86401 | |
| [000.244] | MTASTS policy-->mx | *.checktls.com | |
| [000.272] | _mta-sts.checktls.com | v=STSv1 {DNSSEC} | |
| [000.273] | _mta-sts.checktls.com | id=20200520120000 {DNSSEC} | |
| [000.278] | _smtp._tls.checktls.com | v=TLSRPTv1 {DNSSEC} | |
| [000.279] | _smtp._tls.checktls.com | rua=mailto:sts-reports@checktls.com {DNSSEC} | |
| [000.284] | MX-->checktls.com | (10) mail11-do.checktls.com {DNSSEC} {MTASTS pass} | |
| [000.285] | MX-->checktls.com | (20) mail12-do.checktls.com {DNSSEC} {MTASTS pass} | |
| [000.292] | MX:A-->mail11-do.checktls.com | 134.209.47.28 {DNSSEC} | |
| [000.300] | TLSA-->_25._tcp.mail11-do.checktls.com | 3 1 1 60dcc7761b03dd3d7ec2d7b3eb62553a77cefbee24307eacd142983b704a0270 {DNSSEC} | |
| [000.308] | MX:A-->mail12-do.checktls.com | 104.131.118.193 {DNSSEC} | |
| [000.324] | TLSA-->_25._tcp.mail12-do.checktls.com | 3 1 1 60dcc7761b03dd3d7ec2d7b3eb62553a77cefbee24307eacd142983b704a0270 {DNSSEC} |
| seconds | test stage and result | |
|---|---|---|
| [000.001] | Trying TLS on mail11-do.checktls.com[134.209.47.28:25] (10) @2025-09-19T14:49:14.410907Z | |
| [000.004] | Server answered | |
| [000.093] | SSL/TLS is working correctly on this server | |
| [000.093] | <‑‑ | 220 mail11-do.checktls.com ESMTP Sendmail 8.15.2/8.15.2; Fri, 19 Sep 2025 10:49:14 -0400 |
| [000.094] | We are allowed to connect | |
| [000.094] | ‑‑> | EHLO www2-do.checktls.com |
| [000.139] | <‑‑ | 250-mail11-do.checktls.com Hello www2-do.checktls.com [157.245.11.48], pleased to meet you 250-ENHANCEDSTATUSCODES 250-PIPELINING 250-8BITMIME 250-SIZE 250-AUTH GSSAPI DIGEST-MD5 CRAM-MD5 250-STARTTLS 250-DELIVERBY 250 HELP |
| [000.140] | We can use this server | |
| [000.140] | TLS is an option on this server | |
| [000.141] | ‑‑> | STARTTLS |
| [000.142] | <‑‑ | 220 2.0.0 Ready to start TLS |
| [000.142] | STARTTLS command works on this server | |
| [000.142] | SSL_ocsp_mode = SSL_OCSP_FULL_CHAIN | |
| [000.142] | SSL_hostname (SNI) = mail11-do.checktls.com | |
| [000.171] | Connection converted to SSL/TLS | |
| SSLVersion in use: TLSv1_3 | ||
| Cipher in use: TLS_AES_256_GCM_SHA384 | ||
| Perfect Forward Secrecy: yes | ||
| Session Algorithm in use: Curve X25519 DHE(253 bits) | ||
| [002.811] | MTA-STS pass | |
| [002.811] | DANE pass (match TLSA record(s): #1) | |
| Certificate #1 of 5 (sent by MX): | ||
| Cert signed by: #2 | ||
| Cert VALIDATED: ok | ||
| Cert Hostname VERIFIED (mail11-do.checktls.com = *.checktls.com | DNS:*.checktls.com | DNS:checktls.com) | ||
| cert not revoked by CRL | ||
| cert not revoked by OCSP | ||
Data: |
||
Version: 3 (0x2) |
||
Serial Number: ac:53:4c:0c:a3:65:93:d3 |
||
Validity: |
||
Not Before: Oct 7 12:45:27 2024 GMT |
||
Not After: Nov 8 12:45:27 2025 GMT |
||
Subject: |
||
commonName = *.checktls.com |
||
Issuer: |
||
countryName = US |
||
stateOrProvinceName = Arizona |
||
localityName = Scottsdale |
||
organizationName = GoDaddy.com, Inc. |
||
organizationalUnitName = http://certs.godaddy.com/repository/ |
||
commonName = Go Daddy Secure Certificate Authority - G2 |
||
Subject Public Key Info: |
||
Public Key Algorithm: rsaEncryption |
||
Public Key Bits: (2048 bit) |
||
Modulus:
E4:31:A7:2D:97:0E:EE:86:2B:E4:01:75:23:A9:A2:57
...lines removed for brevity...
50:2F:9F:E1:86:D1:77:F1:FC:DB:A3:F7:CB:67:8E:59 |
||
Exponent: 65537 (0x10001) |
||
Key:
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEA5DGnLZcO7oYr5AF1I6miV+ROvKue86AOQoqpVlz3EO3c5+2qaXlS
f0EySsNwvtD/k+QFyVDEMpFlrlVeugmGJsClsOeCXM4E8vRImP4dj2oPbegvzKG1
RgSwRARJyEwUb7YxSTOwSpmzn8HluA8FntqYA8HEBt2VH2C+0mIoxYS2zBJeYE3g
BIGNSoFJwvQRZpa8Ht2VD8H3VaqFxQQ0alH/QSBiZc8MOR9d/rCmPXBFtcMFB9fE
eNa8O6uSRmWNsqkEwPpYFeIdUwb0b0D8H8/ZGpuCuoPo7e/7V+mTM9kTvKwLh5Z+
O0UziFIHFB0/UC+f4YbRd/H826P3y2eOWQIDAQAB
-----END RSA PUBLIC KEY-----
|
||
X509v3 Extensions: |
||
X509v3 Basic Constraints: critical |
||
CA:FALSE |
||
X509v3 Extended Key Usage: |
||
TLS Web Server Authentication, TLS Web Client Authentication |
||
X509v3 Key Usage: critical |
||
Digital Signature, Key Encipherment |
||
X509v3 CRL Distribution Points: |
||
Full Name:
URI:http://crl.godaddy.com/gdig2s1-31171.crl
|
||
X509v3 Certificate Policies: |
||
Policy: 2.16.840.1.114413.1.7.23.1
CPS: http://certificates.godaddy.com/repository/
Policy: 2.23.140.1.2.1
|
||
Authority Information Access: |
||
OCSP - URI:http://ocsp.godaddy.com/
CA Issuers - URI:http://certificates.godaddy.com/repository/gdig2.crt
|
||
X509v3 Authority Key Identifier: |
||
keyid:40:C2:BD:27:8E:CC:34:83:30:A2:33:D7:FB:6C:B3:F0:B4:2C:80:CE |
||
X509v3 Subject Alternative Name: |
||
DNS:*.checktls.com, DNS:checktls.com |
||
X509v3 Subject Key Identifier: |
||
13:D1:8B:D1:BF:8B:01:0C:9A:D7:2E:27:1A:0D:1C:E4:87:87:CE:80 |
||
CT Precertificate SCTs: |
||
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : 12:F1:4E:34:BD:53:72:4C:84:06:19:C3:8F:3F:7A:13:
F8:E7:B5:62:87:88:9C:6D:30:05:84:EB:E5:86:26:3A
Timestamp : Oct 7 12:45:28.600 2024 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:46:02:21:00:F7:32:DF:A9:B4:ED:D7:D8:41:81:59:
A5:F8:3B:34:52:CE:8A:BE:D9:24:45:C2:0A:81:17:C5:
33:55:75:C6:39:02:21:00:DB:5F:03:83:A0:BC:45:CF:
DA:92:C0:D5:EF:14:FD:DD:05:FD:B0:71:FD:5E:ED:D3:
C9:D9:10:BA:D2:8E:BD:08
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : 7D:59:1E:12:E1:78:2A:7B:1C:61:67:7C:5E:FD:F8:D0:
87:5C:14:A0:4E:95:9E:B9:03:2F:D9:0E:8C:2E:79:B8
Timestamp : Oct 7 12:45:28.773 2024 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:44:02:20:4F:25:B1:C7:2A:51:B0:55:EB:83:F3:21:
4E:75:D8:D5:9B:2B:A9:01:FD:9E:CA:0B:E2:12:7B:D1:
04:73:99:94:02:20:37:81:56:36:47:74:F1:BD:97:BA:
E2:37:0A:63:D1:2F:9B:62:2A:E2:FC:33:63:1C:1D:D5:
67:26:A8:9F:53:A2
Signed Certificate Timestamp:
Version : v1 (0x0)
Log ID : CC:FB:0F:6A:85:71:09:65:FE:95:9B:53:CE:E9:B2:7C:
22:E9:85:5C:0D:97:8D:B6:A9:7E:54:C0:FE:4C:0D:B0
Timestamp : Oct 7 12:45:29.763 2024 GMT
Extensions: none
Signature : ecdsa-with-SHA256
30:45:02:20:09:F5:F4:BB:86:3C:B5:47:73:C4:77:8B:
9D:F5:1E:8B:F4:CB:EA:A3:28:04:45:56:3D:EF:4D:35:
C8:00:C4:77:02:21:00:E3:0D:77:11:68:E7:13:70:1D:
77:43:84:6A:53:1B:CE:05:DB:53:89:52:4A:14:35:75:
4D:51:95:0F:52:E7:26 |
||
Digest: b44887e26447e5cc5c66975fab11897c0a9ccc1b7450efff9d29d3371e6fcbce |
||
Signature: sha256WithRSAEncryption |
||
4e:dd:3b:40:b9:e7:9b:51:1d:de:a4:a2:0e:44:17:70
...lines removed for brevity...
c8:f1:f0:b3:d9:79:1a:2d:f1:5a:66:72:f9:f5:a6:67 |
||
Fingerprints: |
||
all$3082069130820579A003020102020900AC534C0CA36593D3300D0609
...lines removed for brevity...
5A6672F9F5A667 |
||
all$pub$30820122300D06092A864886F70D01010105000382010F003082
...lines removed for brevity...
33885207141D3F502F9FE186D177F1FCDBA3F7CB678E590203010001 |
||
sha256$b44887e26447e5cc5c66975fab11897c0a9ccc1b7450efff9d29d 3371e6fcbce |
||
sha256$pub$60dcc7761b03dd3d7ec2d7b3eb62553a77cefbee24307eacd 142983b704a0270 |
||
sha512$9e73b7f1916e470eeadc5f5387c628476c3ae5f5da3b7c42913ad 2e1f2d47d129f72ea2ffe434a637d279c14cf847b0ae3f580c6a76758fb9 8eed1180c59476f |
||
sha512$pub$4a9227800c6d19024fa77bb9cac655e975c5216bbce1c174c bf382cb3122fe9a0f2917f4fca9ad02d63e03eb4530a474ab94fde11a1e8 0c32ec20df1d81a23fe |
||
Certificate:
-----BEGIN CERTIFICATE-----
MIIGkTCCBXmgAwIBAgIJAKxTTAyjZZPTMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYD
...lines removed for brevity...
XtNWFo2sdTHYWtME6uMKifMcoZPvpR81dg9ifi9TUHifubIGmsjx8LPZeRot8Vpm
cvn1pmc=
-----END CERTIFICATE-----
|
||
| Certificate #2 of 5 (sent by MX): | ||
| Cert signed by: #3, #4 | ||
| Cert VALIDATED: ok | ||
| cert not revoked by CRL | ||
| cert not revoked by OCSP | ||
Data: |
||
Version: 3 (0x2) |
||
Serial Number: 07 |
||
Validity: |
||
Not Before: May 3 07:00:00 2011 GMT |
||
Not After: May 3 07:00:00 2031 GMT |
||
Subject: |
||
countryName = US |
||
stateOrProvinceName = Arizona |
||
localityName = Scottsdale |
||
organizationName = GoDaddy.com, Inc. |
||
organizationalUnitName = http://certs.godaddy.com/repository/ |
||
commonName = Go Daddy Secure Certificate Authority - G2 |
||
Issuer: |
||
countryName = US |
||
stateOrProvinceName = Arizona |
||
localityName = Scottsdale |
||
organizationName = GoDaddy.com, Inc. |
||
commonName = Go Daddy Root Certificate Authority - G2 |
||
Subject Public Key Info: |
||
Public Key Algorithm: rsaEncryption |
||
Public Key Bits: (2048 bit) |
||
Modulus:
B9:E0:CB:10:D4:AF:76:BD:D4:93:62:EB:30:64:B8:81
...lines removed for brevity...
54:35:4B:69:4E:BC:3B:D3:49:2E:1F:DC:C1:D2:52:FB |
||
Exponent: 65537 (0x10001) |
||
Key:
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEAueDLENSvdr3Uk2LrMGS4gQhswwTZYheOL/8+Zc+PzmLmPFIc2hZF
S1WreGtjg2KQzg9pbJnIGhSLTMxFM+qI3J6jryv+gGGdeVfEzy70PzA8XUf8mha8
wzeWQVGOEUtU+Ci+0Iy+8DA4HvOwJvhmR2Nt3nEmR484R1PRRh2049wA6kWsvbxx
2apvANvbzTA6eU9fTEf4He9bwsSdYDuxskOR2KQzTuqz1idPrSWKpcb01dCmrnQF
ZFeItURV1C0qOj74uL3pMgoClGTEFjpQ8Uqu53kzrwwgB3/o3wQ5wmkCbGNS+nfB
G8h0h8i5kxhQVDVLaU68O9NJLh/cwdJS+wIDAQAB
-----END RSA PUBLIC KEY-----
|
||
X509v3 Extensions: |
||
X509v3 Basic Constraints: critical |
||
CA:TRUE |
||
X509v3 Key Usage: critical |
||
Certificate Sign, CRL Sign |
||
X509v3 Subject Key Identifier: |
||
40:C2:BD:27:8E:CC:34:83:30:A2:33:D7:FB:6C:B3:F0:B4:2C:80:CE |
||
X509v3 Authority Key Identifier: |
||
keyid:3A:9A:85:07:10:67:28:B6:EF:F6:BD:05:41:6E:20:C1:94:DA:0F:DE |
||
Authority Information Access: |
||
OCSP - URI:http://ocsp.godaddy.com/ |
||
X509v3 CRL Distribution Points: |
||
Full Name:
URI:http://crl.godaddy.com/gdroot-g2.crl
|
||
X509v3 Certificate Policies: |
||
Policy: X509v3 Any Policy
CPS: https://certs.godaddy.com/repository/
|
||
Digest: 973a41276ffd01e027a2aad49e34c37846d3e976ff6a620b6712e33832041aa6 |
||
Signature: sha256WithRSAEncryption |
||
08:7e:6c:93:10:c8:38:b8:96:a9:90:4b:ff:a1:5f:4f
...lines removed for brevity...
a1:26:7d:0a:09:a7:2e:04:a3:8d:bc:f8:bc:04:30:01 |
||
Fingerprints: |
||
all$308204D0308203B8A003020102020107300D06092A864886F70D0101
...lines removed for brevity...
EDB12D763626DC04EB9FF7611F15DC876FEE469628ADA1267D0A09A72E04
A38DBCF8BC043001 |
||
all$pub$30820122300D06092A864886F70D01010105000382010F003082
...lines removed for brevity...
7487C8B993185054354B694EBC3BD3492E1FDCC1D252FB0203010001 |
||
sha256$973a41276ffd01e027a2aad49e34c37846d3e976ff6a620b6712e 33832041aa6 |
||
sha256$pub$f11c3dd048f74edb7c45192b83e5980d2f67ec84b4ddb9396 e33ff5173ed698f |
||
sha512$42c5b22334cd08c727fdec4aca8df6ec645afa8dd7fc278d26a2c 800c81d7cff86fc107e6d7f28f1a8e4faf0216fd4d2a9af22d69714ca909 9e457d1b2d5188a |
||
sha512$pub$fb48c4f85ae0b07f8ef93d1915e32b161dade3bd070a39df5 08570fd64e7298703f90bffa17fd636c29b8f4a69e8b7b14f0fd6f252520 6f9f47331af89ef79db |
||
Certificate:
-----BEGIN CERTIFICATE-----
MIIE0DCCA7igAwIBAgIBBzANBgkqhkiG9w0BAQsFADCBgzELMAkGA1UEBhMCVVMx
...lines removed for brevity...
LXY2JtwE65/3YR8V3Idv7kaWKK2hJn0KCacuBKONvPi8BDAB
-----END CERTIFICATE-----
|
||
| Certificate #3 of 5 (added from CA Root Store): | ||
| Cert signed by: #3, #4 | ||
| Cert VALIDATED: ok | ||
| cert not revoked by CRL | ||
| cert not revoked by OCSP | ||
Data: |
||
Version: 3 (0x2) |
||
Serial Number: 00 |
||
Validity: |
||
Not Before: Sep 1 00:00:00 2009 GMT |
||
Not After: Dec 31 23:59:59 2037 GMT |
||
Subject: |
||
countryName = US |
||
stateOrProvinceName = Arizona |
||
localityName = Scottsdale |
||
organizationName = GoDaddy.com, Inc. |
||
commonName = Go Daddy Root Certificate Authority - G2 |
||
Issuer: |
||
countryName = US |
||
stateOrProvinceName = Arizona |
||
localityName = Scottsdale |
||
organizationName = GoDaddy.com, Inc. |
||
commonName = Go Daddy Root Certificate Authority - G2 |
||
Subject Public Key Info: |
||
Public Key Algorithm: rsaEncryption |
||
Public Key Bits: (2048 bit) |
||
Modulus:
BF:71:62:08:F1:FA:59:34:F7:1B:C9:18:A3:F7:80:49
...lines removed for brevity...
FC:CE:C4:1B:03:3C:09:EB:49:31:5C:69:46:B3:E0:47 |
||
Exponent: 65537 (0x10001) |
||
Key:
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEAv3FiCPH6WTT3G8kYo/eASVjpIoMTpsUgQwE7hPHmhUmfJ+r2hBtO
oLTbcJjHMgGxBT4HTu70+k8vWTAi56sZVmvigAf88xZ1gDlRe+X5NbZ0TqmNghPk
tj+pA4P6or6KFWp/3gvDthkUBcrqw6gElDtGfDIN8wBmIsiNaW02jBEYt9OyHGC0
OPoCjM7T3UYH3go+6118yHz7sCtTpJJiaVElBWEaRIGMLKlDliPfrDqBmg4pxRyp
6V0etp6eMAo5zvGIgPtLXcwy7IViQyU0AlYnAZG0O3AqP26x6JyIAX2f1PnbU21g
nb8s51iruF9G/M7EGwM8CetJMVxpRrPgRwIDAQAB
-----END RSA PUBLIC KEY-----
|
||
X509v3 Extensions: |
||
X509v3 Basic Constraints: critical |
||
CA:TRUE |
||
X509v3 Key Usage: critical |
||
Certificate Sign, CRL Sign |
||
X509v3 Subject Key Identifier: |
||
3A:9A:85:07:10:67:28:B6:EF:F6:BD:05:41:6E:20:C1:94:DA:0F:DE |
||
Digest: 45140b3247eb9cc8c5b4f0d7b53091f73292089e6e5a63e2749dd3aca9198eda |
||
Signature: sha256WithRSAEncryption |
||
99:db:5d:79:d5:f9:97:59:67:03:61:f1:7e:3b:06:31
...lines removed for brevity...
b4:99:84:65:ca:7a:88:e2:e2:44:be:5c:f7:ea:1c:f5 |
||
Fingerprints: |
||
all$308203C5308202ADA003020102020100300D06092A864886F70D0101
...lines removed for brevity...
7A88E2E244BE5CF7EA1CF5 |
||
all$pub$30820122300D06092A864886F70D01010105000382010F003082
...lines removed for brevity...
2CE758ABB85F46FCCEC41B033C09EB49315C6946B3E0470203010001 |
||
sha256$45140b3247eb9cc8c5b4f0d7b53091f73292089e6e5a63e2749dd 3aca9198eda |
||
sha256$pub$2a8f2d8af0eb123898f74c866ac3fa669054e23c17bc7a95b d0234192dc635d0 |
||
sha512$c509cd5452659ae94c673a47b68e2c0aa8ad177804c8ae2949306 e9232b70ab5b5334d1abe53a25ecaf0c609871b33849773b4edf277dd346 069038f695d76fb |
||
sha512$pub$cb17d366514f38cd029146ff26bc2b054ee12f66cf976f405 920db7f382f4d867996e616da60eac4cb0043edf95c06926a3f57d074d5a 66e5372ef556bd75fd7 |
||
Certificate:
-----BEGIN CERTIFICATE-----
MIIDxTCCAq2gAwIBAgIBADANBgkqhkiG9w0BAQsFADCBgzELMAkGA1UEBhMCVVMx
...lines removed for brevity...
LPAvTK33sefOT6jEm0pUBsV/fdUID+Ic/n4XuKxe9tQWskMJDE32p2u0mYRlynqI
4uJEvlz36hz1
-----END CERTIFICATE-----
|
||
| Certificate #4 of 5 (sent by MX): | ||
| Cert signed by: #5 | ||
| Cert VALIDATED: | ||
| cert not revoked by CRL | ||
| cert not revoked by OCSP | ||
Data: |
||
Version: 3 (0x2) |
||
Serial Number: 1b:e7:15 |
||
Validity: |
||
Not Before: Jan 1 07:00:00 2014 GMT |
||
Not After: May 30 07:00:00 2031 GMT |
||
Subject: |
||
countryName = US |
||
stateOrProvinceName = Arizona |
||
localityName = Scottsdale |
||
organizationName = GoDaddy.com, Inc. |
||
commonName = Go Daddy Root Certificate Authority - G2 |
||
Issuer: |
||
countryName = US |
||
organizationName = The Go Daddy Group, Inc. |
||
organizationalUnitName = Go Daddy Class 2 Certification Authority |
||
Subject Public Key Info: |
||
Public Key Algorithm: rsaEncryption |
||
Public Key Bits: (2048 bit) |
||
Modulus:
BF:71:62:08:F1:FA:59:34:F7:1B:C9:18:A3:F7:80:49
...lines removed for brevity...
FC:CE:C4:1B:03:3C:09:EB:49:31:5C:69:46:B3:E0:47 |
||
Exponent: 65537 (0x10001) |
||
Key:
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEAv3FiCPH6WTT3G8kYo/eASVjpIoMTpsUgQwE7hPHmhUmfJ+r2hBtO
oLTbcJjHMgGxBT4HTu70+k8vWTAi56sZVmvigAf88xZ1gDlRe+X5NbZ0TqmNghPk
tj+pA4P6or6KFWp/3gvDthkUBcrqw6gElDtGfDIN8wBmIsiNaW02jBEYt9OyHGC0
OPoCjM7T3UYH3go+6118yHz7sCtTpJJiaVElBWEaRIGMLKlDliPfrDqBmg4pxRyp
6V0etp6eMAo5zvGIgPtLXcwy7IViQyU0AlYnAZG0O3AqP26x6JyIAX2f1PnbU21g
nb8s51iruF9G/M7EGwM8CetJMVxpRrPgRwIDAQAB
-----END RSA PUBLIC KEY-----
|
||
X509v3 Extensions: |
||
X509v3 Basic Constraints: critical |
||
CA:TRUE |
||
X509v3 Key Usage: critical |
||
Certificate Sign, CRL Sign |
||
X509v3 Subject Key Identifier: |
||
3A:9A:85:07:10:67:28:B6:EF:F6:BD:05:41:6E:20:C1:94:DA:0F:DE |
||
X509v3 Authority Key Identifier: |
||
keyid:D2:C4:B0:D2:91:D4:4C:11:71:B3:61:CB:3D:A1:FE:DD:A8:6A:D4:E3 |
||
Authority Information Access: |
||
OCSP - URI:http://ocsp.godaddy.com/ |
||
X509v3 CRL Distribution Points: |
||
Full Name:
URI:http://crl.godaddy.com/gdroot.crl
|
||
X509v3 Certificate Policies: |
||
Policy: X509v3 Any Policy
CPS: https://certs.godaddy.com/repository/
|
||
Digest: 3a2fbe92891e57fe05d57087f48e730f17e5a5f53ef403d618e5b74d7a7e6ecb |
||
Signature: sha256WithRSAEncryption |
||
59:0b:53:bd:92:86:11:a7:24:7b:ed:5b:31:cf:1d:1f
...lines removed for brevity...
29:09:b0:e1:34:5f:64:77:18:40:51:df:8c:30:a6:af |
||
Fingerprints: |
||
all$3082047D30820365A00302010202031BE715300D06092A864886F70D
...lines removed for brevity...
09B0E1345F6477184051DF8C30A6AF |
||
all$pub$30820122300D06092A864886F70D01010105000382010F003082
...lines removed for brevity...
2CE758ABB85F46FCCEC41B033C09EB49315C6946B3E0470203010001 |
||
sha256$3a2fbe92891e57fe05d57087f48e730f17e5a5f53ef403d618e5b 74d7a7e6ecb |
||
sha256$pub$2a8f2d8af0eb123898f74c866ac3fa669054e23c17bc7a95b d0234192dc635d0 |
||
sha512$b7fd1b90710bbae35395705dd95ee7b03b6ae9ef7f93717c4ea07 b30081d6f22763f0355c82a2ba8bfff1aa1a165b3e4d050464d4feddcdc0 d28240a42e37b7a |
||
sha512$pub$cb17d366514f38cd029146ff26bc2b054ee12f66cf976f405 920db7f382f4d867996e616da60eac4cb0043edf95c06926a3f57d074d5a 66e5372ef556bd75fd7 |
||
Certificate:
-----BEGIN CERTIFICATE-----
MIIEfTCCA2WgAwIBAgIDG+cVMA0GCSqGSIb3DQEBCwUAMGMxCzAJBgNVBAYTAlVT
...lines removed for brevity...
qm5vjLyb4lddJIGvl5echK1srDdMZvNhkREg5L4wn3qkKQmw4TRfZHcYQFHfjDCm
rw==
-----END CERTIFICATE-----
|
||
| Certificate #5 of 5 (sent by MX, also in CA Root Store): | ||
| Cert signed by: #5 | ||
| Cert VALIDATED: | ||
| cert not revoked by CRL | ||
| cert not revoked by OCSP | ||
Data: |
||
Version: 3 (0x2) |
||
Serial Number: 00 |
||
Validity: |
||
Not Before: Jun 29 17:06:20 2004 GMT |
||
Not After: Jun 29 17:06:20 2034 GMT |
||
Subject: |
||
countryName = US |
||
organizationName = The Go Daddy Group, Inc. |
||
organizationalUnitName = Go Daddy Class 2 Certification Authority |
||
Issuer: |
||
countryName = US |
||
organizationName = The Go Daddy Group, Inc. |
||
organizationalUnitName = Go Daddy Class 2 Certification Authority |
||
Subject Public Key Info: |
||
Public Key Algorithm: rsaEncryption |
||
Public Key Bits: (2048 bit) |
||
Modulus:
DE:9D:D7:EA:57:18:49:A1:5B:EB:D7:5F:48:86:EA:BE
...lines removed for brevity...
7E:38:74:C5:F8:FF:B5:69:90:8F:84:74:EA:97:1B:AF |
||
Exponent: 3 (0x3) |
||
Key:
-----BEGIN RSA PUBLIC KEY-----
MIIBCAKCAQEA3p3X6lcYSaFb69dfSIbqvt3/5O9nHPRlaLNXcaBed7vtm0npcIA9
VhhjCG/a8szQP38CVCJUENiygdTAdT1Lf8d3wz54qxoDtSBrL2orscWIfsS7HrDB
2EUnb6o3WPeHJtfYLfapF7cfcjZOphc/ZZiS2ypuXaL+iOAL3n/ljRXh68s61eIS
ohMt2I6vXxI9oAgFCLZcpWU4BEWZHqNgYHTFQaVyYhtixR9vXxpCvgJRZaiuIxhq
/HgDqU1/gMP6q1r8oUCkyhkW/rLI715zDe53vZr2eZi8sQdnohUN3aBYxkR7Cj5i
KF+6QQdTWM8Rfjh0xfj/tWmQj4R06pcbrwIBAw==
-----END RSA PUBLIC KEY-----
|
||
X509v3 Extensions: |
||
X509v3 Subject Key Identifier: |
||
D2:C4:B0:D2:91:D4:4C:11:71:B3:61:CB:3D:A1:FE:DD:A8:6A:D4:E3 |
||
X509v3 Authority Key Identifier: |
||
keyid:D2:C4:B0:D2:91:D4:4C:11:71:B3:61:CB:3D:A1:FE:DD:A8:6A:D4:E3
DirName:/C=US/O=The Go Daddy Group, Inc./OU=Go Daddy Class 2 Certification Authority
serial:00
|
||
X509v3 Basic Constraints: |
||
CA:TRUE |
||
Digest: c3846bf24b9e93ca64274c0ec67c1ecc5e024ffcacd2d74019350e81fe546ae4 |
||
Signature: sha1WithRSAEncryption |
||
32:4b:f3:b2:ca:3e:91:fc:12:c6:a1:07:8c:8e:77:a0
...lines removed for brevity...
28:9c:b1:b9:2a:5a:57:ad:37:0f:af:1d:7f:db:bd:9f |
||
Fingerprints: |
||
all$30820400308202E8A003020102020100300D06092A864886F70D0101
...lines removed for brevity...
57AD370FAF1D7FDBBD9F |
||
all$pub$30820120300D06092A864886F70D01010105000382010D003082
...lines removed for brevity...
BA41075358CF117E3874C5F8FFB569908F8474EA971BAF020103 |
||
sha256$c3846bf24b9e93ca64274c0ec67c1ecc5e024ffcacd2d74019350 e81fe546ae4 |
||
sha256$pub$5632d97bfa775bf3c99ddea52fc2553410864016729c52dd6 524c8a9c3b4489f |
||
sha512$2df98b9df476d49399f0bd7f74627356cbf0e231bdd15575b0320 6a8c52bc6a010790543cd79a5d85254c9b7bde708ba1cfc03ab2138bdcc8 0004b88333d9843 |
||
sha512$pub$39867a78b54bfc408ef5e11481b65f7e1a166990068073910 98dabe4b0c13a0befcb5612583314cd5b23e396ccacba827224d0ea39d06 72548e66e69258822bb |
||
Certificate:
-----BEGIN CERTIFICATE-----
MIIEADCCAuigAwIBAgIBADANBgkqhkiG9w0BAQUFADBjMQswCQYDVQQGEwJVUzEh
...lines removed for brevity...
ReYNnyicsbkqWletNw+vHX/bvZ8=
-----END CERTIFICATE-----
|
||
| [002.853] | ~~> | EHLO www2-do.checktls.com |
| [002.898] | <~~ | 250-mail11-do.checktls.com Hello www2-do.checktls.com [157.245.11.48], pleased to meet you 250-ENHANCEDSTATUSCODES 250-PIPELINING 250-8BITMIME 250-SIZE 250-AUTH GSSAPI DIGEST-MD5 CRAM-MD5 LOGIN PLAIN 250-DELIVERBY 250 HELP |
| [002.899] | SSL/TLS is working correctly on this server | |
| [002.899] | ~~> | MAIL FROM:<test@checktls.com> |
| [002.946] | <~~ | 250 2.1.0 <test@checktls.com>... Sender ok |
| [002.946] | Sender is OK | |
| [002.947] | ~~> | QUIT |
| [002.948] | <~~ | 221 2.0.0 mail11-do.checktls.com closing connection |
Example results from the CheckTLS ("TestSender") Test
(scroll left and right to see wide data)SUCCESSFUL //email/test From: (V01.65.07)
Your email was sent securely using TLS.
Just a reminder that CheckTLS.com (and these tests) are NOT free. Please support us, thank you.
| SENDER | Connection | 104.131.168.30(mailbox1-do.checktls.com) | ||
| SENDER | Header | From | test@checktls.com | |
| SENDER | Header | Date | Thu, 27 Nov 2025 11:40:47 -0500 | |
| SENDER | Header | Subject | YourPasswordHere | |
| SENDER | ClientCert | -----BEGIN CERTIFICATE----- MIIHxDCCBqygAwIBAgIJAKoqBUM2KO7dMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYD VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEa MBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0 cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2Vj dXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTI1MTAwNzIxMTMyNVoX DTI2MTEwODIxMTMyNVowGTEXMBUGA1UEAwwOKi5jaGVja3Rscy5jb20wggEiMA0G CSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCVN7v2C8hX29ddIAKRqlhdiz8C71NV mEaFFrHQISNQwifUx6vX4l81JtMcKA9zybPY4iHVPRB5lg/8hiGGA0c83DpxZgXf 07e99BDaoHFedn6eFh5+xH/wPr56uJX4eZzx5W2CPAv2IZcBi5QwId6HlFZAhoDa hgqxkeM1h8FlEJcbNOATObq9gv3T8MJ74iwX69qbZ6BXkYmj6TXWFmTsD4Nx1815 ifSj5M4ut7sqbWtHEBrHYxzEPN1F+htwPJupzs4oeTQoD1+3sfAUqZl3KpSXd//O T3v25HdNPwwZb9Fs4HE5pG60aBLyxuJjqJJipqGAr4DeRi7uGtlsksGbAgMBAAGj ggRxMIIEbTAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEF BQcDAjAOBgNVHQ8BAf8EBAMCBaAwOQYDVR0fBDIwMDAuoCygKoYoaHR0cDovL2Ny bC5nb2RhZGR5LmNvbS9nZGlnMnMxLTY0NzAzLmNybDBdBgNVHSAEVjBUMAgGBmeB DAECATBIBgtghkgBhv1tAQcXATA5MDcGCCsGAQUFBwIBFitodHRwOi8vY2VydGlm aWNhdGVzLmdvZGFkZHkuY29tL3JlcG9zaXRvcnkvMHYGCCsGAQUFBwEBBGowaDAk BggrBgEFBQcwAYYYaHR0cDovL29jc3AuZ29kYWRkeS5jb20vMEAGCCsGAQUFBzAC hjRodHRwOi8vY2VydGlmaWNhdGVzLmdvZGFkZHkuY29tL3JlcG9zaXRvcnkvZ2Rp ZzIuY3J0MB8GA1UdIwQYMBaAFEDCvSeOzDSDMKIz1/tss/C0LIDOMIIBWQYDVR0R BIIBUDCCAUyCDiouY2hlY2t0bHMuY29tggxjaGVja3Rscy5jb22CESouZW1haWxz ZW50cnkuY29tgg9lbWFpbHNlbnRyeS5jb22CECouZW1haWwtdGVzdC5jb22CDmVt YWlsLXRlc3QuY29tgh0qLmluZm9ybWF0aW9uc2VjdXJpdHl0ZXN0LmNvbYIbaW5m b3JtYXRpb25zZWN1cml0eXRlc3QuY29tgiAqLmluZm9ybWF0aW9uc2VjdXJpdHl0 ZXN0aW5nLmNvbYIeaW5mb3JtYXRpb25zZWN1cml0eXRlc3RpbmcuY29tgg8qLnNu aWZmeW5ldC5jb22CDXNuaWZmeW5ldC5jb22CDyouc25pZmZpbmV0LmNvbYINc25p ZmZpbmV0LmNvbYIUKi5pbmZvc2VjdGVzdGluZy5jb22CEmluZm9zZWN0ZXN0aW5n LmNvbTAdBgNVHQ4EFgQUOJ9V4Vko/qK+PUK4v+kSgIaeFn8wggF9BgorBgEEAdZ5 AgQCBIIBbQSCAWkBZwB2ANdtfRDRp/V3wsfpX9cAv/mCyTNaZeHQswFzF8DIxWl3 AAABmcCFnXUAAAQDAEcwRQIgYz0T15X0w0lhAjfJs65OuKI5ccqnLLnEzaTyAMje hDMCIQD9YuSfxV+OEm69bNvLTvMxOCze5A2NnAe83B85XwYOcAB1AKyrMHBs6+yE MfQT0vSRXxEeQiRDsfKmjE88KzunHgLDAAABmcCFoI0AAAQDAEYwRAIgGlBi1ktw eCuPSQMbv7GwA35ZHoFxV00mqZvZh3pSv9ICIGCnXCOn1ZixPCguNpbopdHEijN0 2lv0G4wrZF17GQfrAHYAwjF+V0UZo0XufzjespBB68fCIVoiv3/Vta12mtkOUs0A AAGZwIWhOAAABAMARzBFAiEAxnTCST3cPxpK3W8xWxBJnGgpRArX2BBYQvR1zFG1 J7gCIBwLZYXpRrZsLx5cKutUUGacqgPyiKBb6qR4HdvweFwXMA0GCSqGSIb3DQEB CwUAA4IBAQBCN8ARNr26j4QhhPbXLXl4Cs+YNgtamdjPT1viYxN5hZCtg7uP7jiW EDBzvMDMngp1l2MUGyAWM3XavC09+CRPB91ChU450NN/VyGYytU25CUz0uTiIgmf jka/C/KZMFhTUbVh88dStuz42oOgHMFso7j7LR6EGvZAIopxEOtIaEGy+zR6Yn1Z i2kUBxHCjHfkytKeG+ziooNivJhwyA+aHWhRcNcs3n+RyNblLjvPKnu5H+rToJmP aXdkd2Yd2nQXPsMiZy5fS8scMZsV0II/658Lk1kRS0G//e0zlyQpbXpVxIRWyo5q 8N40EZXuxyxRlr1WLOdVskHIFyKfdCZH -----END CERTIFICATE----- |
||
| SENDER | SNI | [none] | ||
| TLS | info | SSLVersion | TLSv1_3 | |
| TLS | info | SSLCipher | TLS_AES_256_GCM_SHA384 | |
| TLS | result | Successful | ||
| SPF | DNS | checktls.com | TXT | {DNSSEC}"v=spf1 a mx a:whitelist.checktls.com a:spf.checktls.com -all", {DNSSEC}"v=spf1 a mx a:whitelist.checktls.com a:spf.checktls.com -all" |
| SPF | DNS | mailbox1-do.checktls.com | TXT | {DNSSEC}"v=spf1 a -all", {DNSSEC}"v=spf1 a -all" |
| SPF | mfrom | record | v=spf1 a mx a:whitelist.checktls.com a:spf.checktls.com -all | |
| SPF | mfrom | text | pass (Mechanism 'a:whitelist.checktls.com' matched) | |
| SPF | mfrom | local | checktls.com: 104.131.168.30 is authorized to use 'checktls.com' in 'mfrom' identity (mechanism 'a:whitelist.checktls.com' matched) | |
| SPF | mfrom | header | Received-SPF: pass (checktls.com: 104.131.168.30 is authorized to use 'checktls.com' in 'mfrom' identity (mechanism 'a:whitelist.checktls.com' matched)) receiver=ts11-do.checktls.com; identity=mailfrom; envelope-from=checktls.com; helo=localhost; client-ip=104.131.168.30 | |
| SPF | mfrom | result | pass | |
| SPF | helo | record | v=spf1 a -all | |
| SPF | helo | text | pass (Mechanism 'a' matched) | |
| SPF | helo | local | mailbox1-do.checktls.com: 104.131.168.30 is authorized to use 'mailbox1-do.checktls.com' in 'helo' identity (mechanism 'a' matched) | |
| SPF | helo | header | Received-SPF: pass (mailbox1-do.checktls.com: 104.131.168.30 is authorized to use 'mailbox1-do.checktls.com' in 'helo' identity (mechanism 'a' matched)) receiver=ts11-do.checktls.com; identity=helo; helo=mailbox1-do.checktls.com; client-ip=104.131.168.30 | |
| SPF | helo | result | pass | |
| DKIM | SIGNATURE | IDENTITY | @checktls.com | |
| DKIM | SIGNATURE | DETAIL | pass | |
| DKIM | SIGNATURE | DOMAIN | checktls.com | |
| DKIM | SIGNATURE | HASH_ALGORITHM | sha1 | |
| DKIM | SIGNATURE | CANONICALIZATION | relaxed | |
| DKIM | SIGNATURE | HEADER_LIST | from:to:subject:date:bimi-selector | |
| DKIM | SIGNATURE | BODY_HASH | W4h/LkgaecT8G6jePsCkR7DBk+s= | |
| DKIM | SIGNATURE | DATA | geDVY6wWk8d8Im1syMG9kZA1m6BjMb8DRmFNYvNuLARN7WIRt4YFJ88brR81SzlWmYSuzxQwtVglkKGjVKYtYYXcg5wYfmVB1kQoGI1MhugdTmRdzxqTJjmlOMzUM+NCDoJJsFarmCY8W7E+eNYHjVJPdjimsRTDHU/3i0VouuU=ouuU= | |
| DKIM | DNS | default._domainkey.checktls.com | TXT | "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCkZxaMIXWH8NqafDS6Kzr6eNwlofpu+50Y+t9GpgXnCgt3mZTeoFr4kXcxNNfibzDHafcm8aT+Es3t1TOxlhYiqlyi60cVgRajwryRMkPCD4SvxU97V6gj5VFhfz1VtyaHUXYbJnGxShluWPa4AbXMmqey7dNDCPQKl5aOkILdPQIDAQAB" |
| DKIM | DNS | v= | DKIM1 | |
| DKIM | DNS | p= | MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCkZxaMIXWH8NqafDS6Kzr6eNwlofpu+50Y+t9GpgXnCgt3mZTeoFr4kXcxNNfibzDHafcm8aT+Es3t1TOxlhYiqlyi60cVgRajwryRMkPCD4SvxU97V6gj5VFhfz1VtyaHUXYbJnGxShluWPa4AbXMmqey7dNDCPQKl5aOkILdPQIDAQAB | |
| DKIM | DNS | k= | rsa | |
| DKIM | SIGNATURE | DIGEST | B670B21EC8FE440BE7D0CA37E2E5804B86613EA1 |
|
| DKIM | CANONICAL | HEADERS | from:<test@checktls.com>
to:<test@TestSender.CheckTLS.com> subject:YourPasswordHere date:Thu, 27 Nov 2025 11:40:47 -0500 bimi-selector:v=BIMI1; s=default; dkim-signature:v=1; a=rsa-sha1; c=relaxed/simple; d=checktls.com; s=default; t=1764261647; bh=W4h/LkgaecT8G6jePsCkR7DBk+s=; h=From:To:Subject:Date:BIMI-Selector; b= |
|
| DKIM | COMPUTED | BODY_HASH | W4h/LkgaecT8G6jePsCkR7DBk+s= |
|
| DKIM | COMPUTED | DIGEST | B670B21EC8FE440BE7D0CA37E2E5804B86613EA1 |
|
| DKIM | POLICY | sender | "o=-", location="checktls.com", result="accept" | |
| DKIM | POLICY | author | "o=~" (default), result="accept" | |
| DKIM | POLICY | ADSP | "" (default), result="accept" | |
| DKIM | result | pass | ||
| DMARC | DNS | _dmarc.checktls.com | TXT | {DNSSEC}"v=DMARC1; p=quarantine; rua=postmaster@checktls.com" |
| DMARC | dkim_align | strict | ||
| DMARC | published | p | quarantine | |
| DMARC | published | rua | postmaster@checktls.com | |
| DMARC | published | v | DMARC1 | |
| DMARC | published | domain | checktls.com | |
| DMARC | disposition | none | ||
| DMARC | dkim_meta | selector | default | |
| DMARC | dkim_meta | identity | ||
| DMARC | dkim_meta | domain | checktls.com | |
| DMARC | spf_align | strict | ||
| DMARC | spf | pass | ||
| DMARC | dkim | pass | ||
| DMARC | result | pass | ||
| BIMI | DNS | default._bimi.checktls.com | TXT | {DNSSEC}v=BIMI1\;l=https://www.checktls.com/images/checktlsbimi.svg\;a=self\;, {DNSSEC}v=BIMI1\;l=https://www.checktls.com/images/checktlsbimi.svg\;a=self\; |
| BIMI | domain | checktls.com | ||
| BIMI | header | v=BIMI1; s=default; | ||
| BIMI | selector | default | ||
| BIMI | headers | BIMI-Indicator | ||
| BIMI | headers | BIMI-Location | v=BIMI1; l=https://www.checktls.com/images/checktlsbimi.svg |
|
| BIMI | result | pass | ||
The transcript of the eMail SMTP session is below, with:
--> this is a line from your email system to us (~~> when encrypted)
<-- this is a line to your email system from us (<~~ when encrypted)
=== this is a line about the tls negotiation (cypher, cert, etc)
*** this is an error, warning, or info line that the test found
<-- 220 localhost ESMTP TestSender(V01.65.07) Thu, 27 Nov 2025 11:40:47 -0500
-> EHLO mailbox1-do.checktls.com
<-- 250-localhost Hello mailbox1-do.checktls.com [104.131.168.30], pleased to meet you
<-- 250-ENHANCEDSTATUSCODES
<-- 250-8BITMIME
<-- 250-STARTTLS
<-- 250 HELP
--> STARTTLS
<-- 220 Ready to start TLS
=== TLS started with cipher TLSv1_3:TLS_AES_256_GCM_SHA384
=== TLS client cert:
Subject Name: /CN=*.checktls.com
Issuer Name: /C=US/ST=Arizona/L=Scottsdale/O=GoDaddy.com, Inc./OU=http://certs.godaddy.com/repository//CN=Go Daddy Secure Certificate Authority - G2
~~> EHLO mailbox1-do.checktls.com
<~~ 250-localhost Hello mailbox1-do.checktls.com [104.131.168.30], pleased to meet you
<~~ 250-ENHANCEDSTATUSCODES
<~~ 250-8BITMIME
<~~ 250 HELP
~~> MAIL FROM:<test@checktls.com>
<~~ 250 Ok - mail from test@checktls.com
~~> RCPT TO:<test@TestSender.CheckTLS.com>
<~~ 250 Ok - recipient test@TestSender.CheckTLS.com
~~> DATA
<~~ 354 Send data. End with CRLF.CRLF
~~> DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/simple; d=checktls.com; s=default;
~~> t=1764261647; bh=W4h/LkgaecT8G6jePsCkR7DBk+s=;
~~> h=From:To:Subject:Date:BIMI-Selector;
~~> b=geDVY6wWk8d8Im1syMG9kZA1m6BjMb8DRmFNYvNuLARN7WIRt4YFJ88brR81SzlWm
~~> YSuzxQwtVglkKGjVKYtYYXcg5wYfmVB1kQoGI1MhugdTmRdzxqTJjmlOMzUM+NCDoJ
~~> JsFarmCY8W7E+eNYHjVJPdjimsRTDHU/3i0VouuU=ouuU=
~~> From: <test@checktls.com>
~~> To: <test@TestSender.CheckTLS.com>
~~> Subject: YourPasswordHere
~~> Date: Thu, 27 Nov 2025 11:40:47 -0500
~~> BIMI-Selector: v=BIMI1; s=default;
~~>
~~> TLS
~~> Headers
~~> SSLVERSION
~~> SSLCIPHER
~~> SNI
~~> ClientCert
~~> SPF
~~> DKIM
~~> DMARC
~~> DNS
~~> DNSSEC
~~> BIMI
~~> SMTP
~~> .
<~~ 250 Ok
~~> QUIT
<~~ 221 localhost closing connection
